Mastering SSH Key Management: Best Practices & Security Tips
Are your digital fortresses truly secure, or are you leaving the back door ajar? Effective SSH key management is not merely a technical detail; it's the bedrock upon which secure remote access and robust infrastructure security are built.
The modern digital landscape is rife with threats, and organizations of all sizes face a constant barrage of attacks. A single weak point can compromise an entire system, leading to data breaches, regulatory penalties, and irreparable reputational damage. Among the most critical components of any security strategy is the management of Secure Shell (SSH) keys. These cryptographic keys are the gatekeepers to your servers, encapsulating and encrypting data transmission over networks. Their effective management is no longer optional; it's a fundamental necessity.
This comprehensive guide delves into the world of SSH key management, providing a roadmap for securing your infrastructure and safeguarding your sensitive data. We will explore best practices, from generating key pairs and implementing rotation policies to leveraging automation and adhering to regulatory compliance.
- Unveiling Anime Archetypes Your Guide To Common Character Types
- Laurence Mason Net Worth 2024 Updates Career Insights
At its core, SSH key management is about control. Without it, your organization is vulnerable. Unmanaged SSH keys can be a significant attack vector. They can lead to policy violations, failed audits, and crippling regulatory penalties. This is why a structured approach to SSH key management is so critical. This approach requires a combination of technical expertise, policy development, and diligent execution. Its an ongoing process, not a one-time fix, and demands constant vigilance and adaptation to the evolving threat landscape.
One of the most significant challenges organizations face is the sheer scale of SSH keys. As the number of systems and users grows, so does the number of keys. Manual key management quickly becomes unwieldy and prone to errors. Automation becomes not just desirable but essential. With automation, you can streamline key generation, distribution, rotation, and removal, significantly reducing the overhead and risk associated with manual processes.
Consider the following table which highlights the critical aspects of SSH key management:
- Mark Hyman News Relationships Health Insights Latest
- Maz Jobrani Preetha Jobrani A Look At Their Life Together
| Area | Description | Best Practices |
|---|---|---|
| Key Generation | The process of creating SSH key pairs (public and private). |
|
| Key Storage and Protection | Securing the storage and access to private keys. |
|
| Key Rotation | Regularly changing SSH keys. |
|
| Key Auditing and Monitoring | Tracking key usage and identifying potential issues. |
|
| Key Lifecycle Management | Managing the entire lifecycle of SSH keys from generation to destruction. |
|
For more information, you can refer to the National Institute of Standards and Technology (NIST) Special Publication 800-57, which provides comprehensive guidance on key management.
NIST Special Publication 800-57
Properly managing SSH keys is not just a technical issue; it's a fundamental aspect of access management. Implementing a robust SSH key management strategy is crucial for achieving and maintaining a strong security posture. This includes defining clear policies, deploying appropriate tools, and establishing efficient processes. Only then can you mitigate the risks associated with unauthorized access, data breaches, and regulatory non-compliance.
At the heart of secure SSH communication lies the power of cryptographic keys. These keys are generated in pairs, a public key and a corresponding private key. The public key is distributed and used to encrypt data, while the private key is kept secret and used to decrypt the data. Properly generating these key pairs is essential. Its the first, and perhaps most crucial, step.
To properly generate SSH key pairs, it's vital to adhere to several best practices:
- Choose a strong cryptographic algorithm: RSA keys should be at least 4096 bits long. Consider using Ed25519 for better performance and security.
- Protect your private key with a passphrase: This adds an extra layer of security, preventing unauthorized access even if the key is compromised.
- Use dedicated key generation tools: OpenSSH provides the `ssh-keygen` utility, which is the standard tool for generating keys on most Linux and macOS systems.
- Consider using Hardware Security Modules (HSMs) or Smart Cards: For enhanced security, store private keys on hardware-backed devices that provide an extra layer of protection.
Once you have generated your key pairs, the next step is to manage them effectively. This includes the entire lifecycle, from creation to deletion. This involves secure storage, regular rotation, and controlled access.
Here are the best practices for managing SSH keys:
- Inventory your keys: Understand the scope of your keys, what they are used for, and where they are deployed.
- Rotate keys regularly: This practice limits the potential impact of a compromised key. Establish a regular rotation schedule based on your security requirements, typically between 90 days to 1 year.
- Assign one key per user: Minimizes the risk of key misuse, making it easier to identify and revoke compromised keys.
- Audit regularly: Review your SSH key usage logs to identify any suspicious activity or unauthorized access attempts.
- Automate processes: Employ automation tools to streamline key generation, deployment, and rotation, thus reducing manual errors and improving efficiency.
- Utilize namespaces: Organize keys based on user, system, or function to make management more efficient.
- Implement access controls: Restrict access to private keys to authorized personnel only. Implement strict access controls for key storage and usage.
The importance of robust SSH key management cannot be overstated. It is an integral part of any comprehensive cybersecurity strategy, directly impacting an organization's ability to secure remote access to its systems and safeguard its data. Ignoring this critical aspect of IT infrastructure security exposes your organization to significant risks, including unauthorized access, data breaches, and regulatory penalties. A well-defined SSH key management strategy, when implemented effectively, enhances overall security posture and ensures business continuity by minimizing the potential for security incidents.
Implementing namespaces in SSH key management is another best practice worth considering. Namespaces allow you to organize keys logically, based on factors such as user, system, or function. This approach simplifies key management, making it easier to track and control access. For example, you might create a namespace for each department within your organization, or for each type of system (e.g., production, development). This improves visibility and simplifies key revocation when necessary.
Automation is another crucial aspect of effective SSH key management. Given the vast number of SSH keys that enterprises manage, manual processes are simply infeasible. Automation tools can streamline key generation, rollouts, rotations, and removal, significantly reducing the overhead and risk associated with manual key lifecycle management. Automation not only improves efficiency but also enhances security, because it removes human error from the equation. Fully automating SSH key lifecycle processes should be a priority for any organization seeking to improve its security posture.
You can consider the use of tools and solutions that integrate with your existing infrastructure and offer features such as:
- Centralized key storage and management.
- Automated key rotation and revocation.
- Integration with identity management systems.
- Audit trails and reporting.
Consider the use of OpenSSH certificates. OpenSSH certificates allow you to establish trust and manage access without distributing private keys to every user. With certificates, you can sign public keys, allowing users to authenticate to your systems. This approach simplifies key management, enhances security, and makes it easier to manage access control.
When considering a solution, evaluate its features, compatibility, and ease of integration with your existing systems. A successful implementation requires careful planning, robust execution, and ongoing monitoring to ensure compliance and effectiveness.
A real solution requires addressing authorized keys. Not all keys are created equal. Some keys may have broader access privileges than others. Identify privileged keys used for critical operations like signing or access to sensitive data. Regularly audit these keys and rotate them more frequently.
SSH key management can be effectively tackled by the core security teams, as it's an access management issue. It involves a combination of technical knowledge, policy development, and process implementation. Ensure that the core security teams are equipped with the resources, training, and authority necessary to manage SSH keys effectively.
With SSH being the primary method for remote system administration, it's essential to implement proper hardening techniques to protect against unauthorized access and potential attacks.
Hardening techniques include:
- Disable password-based authentication: Only allow key-based authentication.
- Change the default SSH port: This can reduce the number of automated attacks.
- Limit the number of failed login attempts: Protect against brute-force attacks.
- Use a firewall to restrict SSH access: Allow access only from trusted IP addresses.
- Regularly update the SSH server software: Apply security patches to address vulnerabilities.
In the context of key management, it is important to document and harmonize rules and practices for key lifecycle management (generation, distribution, and destruction).
In conclusion, securing SSH access to your Linux systems is a critical step in maintaining a robust security posture. Implementing the best practices outlined above will significantly reduce the risk of unauthorized access, improve your overall security posture, and ensure regulatory compliance. Remember that effective SSH key management is an ongoing process that requires continuous monitoring, adaptation, and improvement to meet the evolving demands of the threat landscape.
- Ari Kytsya On Tiktok Viral Starbucks Video Uncovered
- Josephine Archer Cameron The Untold Story Of Linda Hamiltons Daughter
SSH Key Management Explained Best Practices & More StrongDM
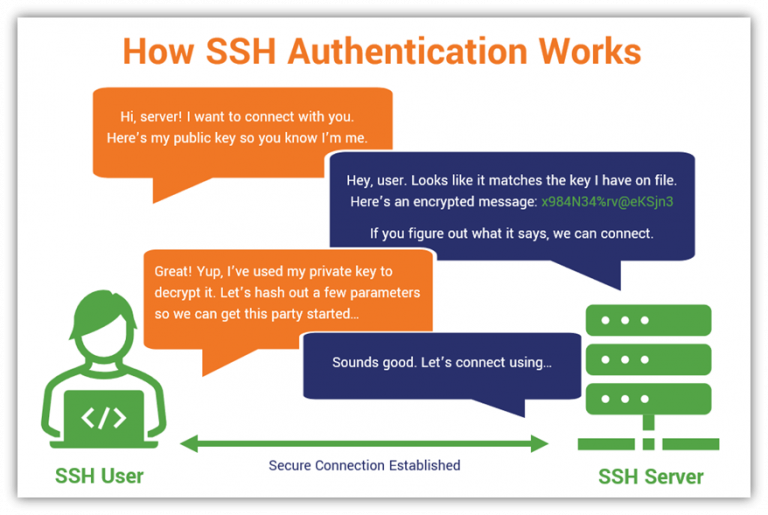
14 SSH Key Management Best Practices You Need to Know Hashed Out by
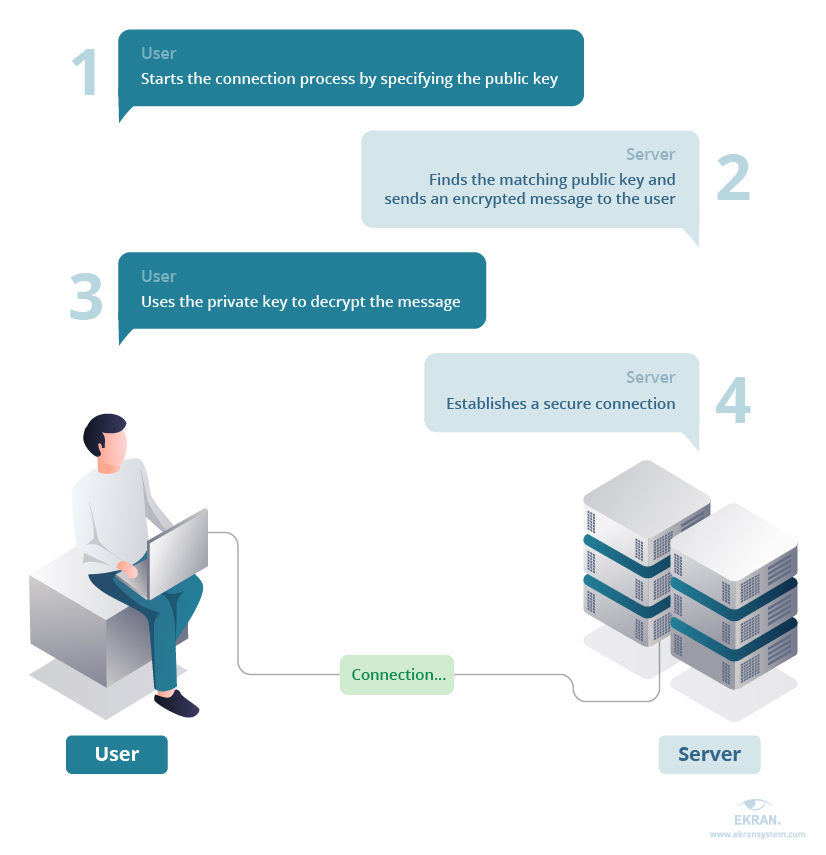
Secure Socket Shell (SSH) Key Management Overview & Best Practices