Secure Remote IoT P2P: Your Guide To Security & Efficiency
In an era defined by hyper-connectivity, can we truly safeguard the flow of information and maintain control over our increasingly smart devices? The answer lies within the rapidly evolving landscape of Remote IoT P2P technology, a paradigm shift that promises to redefine how we interact with the digital world.
From the fundamental principles to the intricacies of advanced implementations, understanding Remote IoT P2P is no longer a luxury but a necessity. It's a journey into the heart of a technological revolution, where devices communicate directly, bypassing the traditional centralized structures and fostering unparalleled levels of security, efficiency, and autonomy. This article will serve as your comprehensive guide, navigating the nuances, potential benefits, and critical considerations of this transformative technology.
A brief look at the history of IoT and P2P unveils the foundation upon which this technological marvel is built. The Internet of Things (IoT), a network of interconnected devices, has evolved from simple data collection to complex automation. Simultaneously, Peer-to-Peer (P2P) technology, where devices communicate directly with each other without relying on a central server, has been steadily gaining traction. The convergence of these two forces has given birth to Remote IoT P2P, a powerful solution that offers a more secure, scalable, and efficient way to manage IoT devices.
One of the core strengths of this approach is its emphasis on data privacy and network security. In a world where data breaches and surveillance are constant concerns, Remote IoT P2P offers a robust shield. With direct device-to-device communication, the risk of data interception and unauthorized access is significantly reduced. This is particularly critical for sensitive applications such as healthcare monitoring, financial transactions, and critical infrastructure management.
Let's delve into the mechanics. A P2P IoT network empowers devices to share resources, exchange data, and provide services without the need for a central server. This decentralized structure eliminates single points of failure, improves scalability, and reduces latency. Platforms designed for implementing P2P IoT are engineered to deliver enhanced fault tolerance, ensuring continued operation even when individual devices or network segments encounter issues.
The advantages are numerous. Scalability, allowing the network to effortlessly grow as more devices are added, and reduced latency, making communication faster and more responsive, are key benefits. Think of a smart city initiative where sensors deployed across the urban landscape transmit real-time data. With Remote IoT P2P, this data can flow seamlessly between devices, from streetlights to traffic cameras, without the delays and bottlenecks associated with centralized architectures.
- Ximena Saenz Age Net Worth Boyfriend All You Need To Know
- Vicki Mckenna From Marxism To Conservative Talk Show Host Full Story
Securing Remote IoT Devices: A Practical Deep Dive
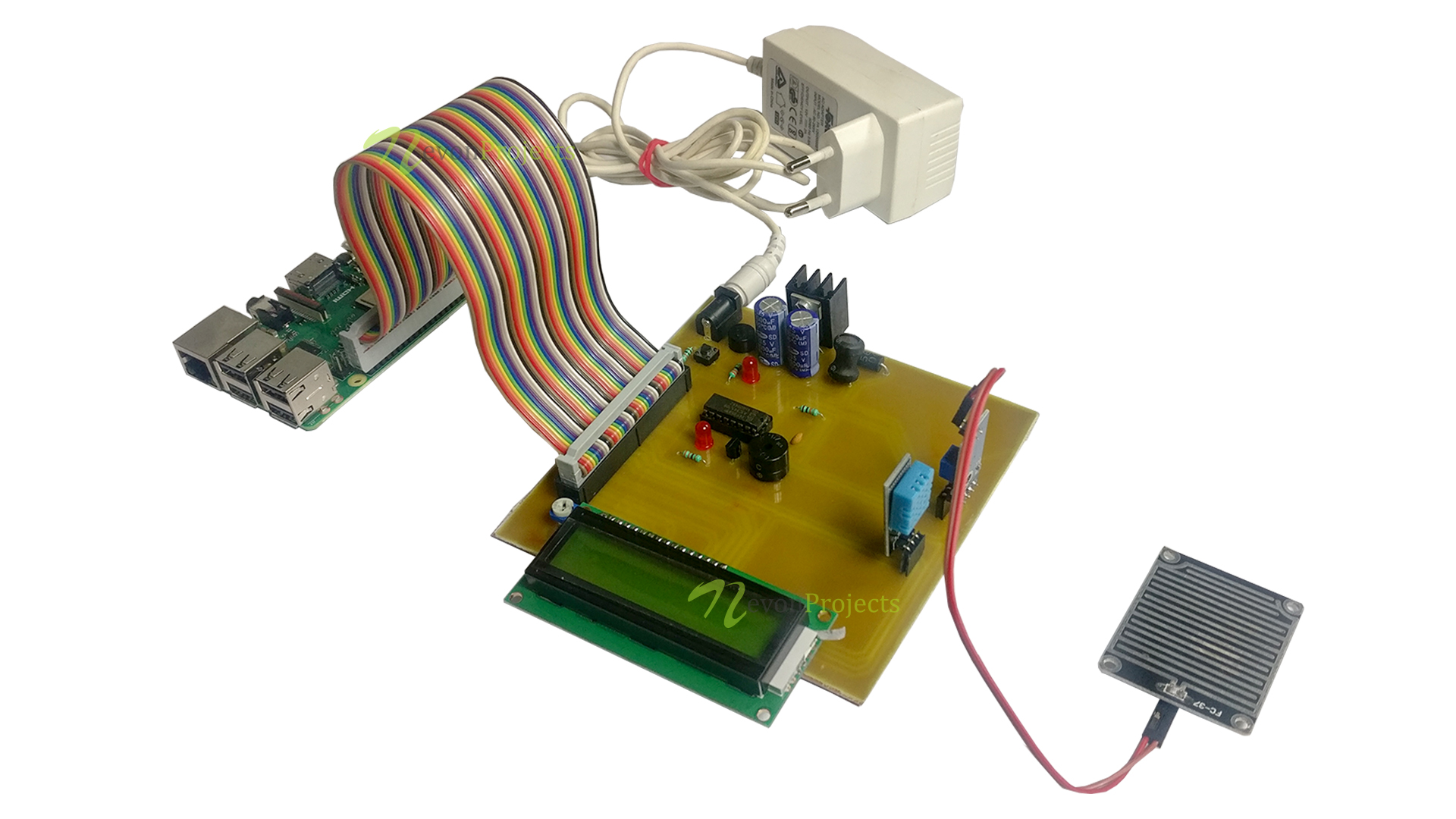
Central to the success of Remote IoT P2P is the ability to secure the connections. Consider the practical application of securing remote IoT devices using P2P SSH on a Raspberry Pi. This requires a combination of best practices, robust tools, and meticulous configuration. By adhering to the guidelines outlined in this article, you can ensure your IoT network remains safe and efficient, able to withstand the ever-present threats of cyberattacks.
Connecting remote IoT devices through P2P SSH on a Raspberry Pi presents a powerful method for managing and controlling your network from any location. From this vantage point, you can monitor device status, issue commands, and perform necessary maintenance. However, as with any technology, security should always be a top priority. A comprehensive security strategy is crucial.
This guide will walk you through the process of establishing a secure connection. It will navigate through the steps of setting up a secure connection between your IoT devices, utilizing P2P SSH on a Raspberry Pi, and ensuring seamless compatibility with Windows systems.
The remote IoT P2P VPC network establishes direct connections, allowing for rapid data communication between IoT devices. This is achieved with minimal latency and maximized bandwidth. In the realm of AI-driven IoT applications, this translates into enhanced connectivity and operational efficiency. Explore practical remote IoT P2P examples that leverage AI for enhanced connectivity and efficiency.
Securing remote IoT connections using P2P SSH is paramount to preserving sensitive data and maintaining the integrity of your IoT networks. It acts as a first line of defense against unauthorized access and potential cyberattacks. By implementing these best practices, organizations can dramatically enhance their cybersecurity posture and mitigate the risks associated with cyber threats.
P2P SSH: Ubuntu Example
In today's interconnected world, securing remote IoT P2P SSH, for instance on Ubuntu, is a critical area of focus. As more devices become connected to the internet, the need for secure communication and data transfer has never been more important. The risk of data breaches, unauthorized access, and system compromise is very real. Comprehensive security measures have become a necessity, not a luxury.
Data privacy is a critical aspect of IoT security, requiring meticulous attention. Securely connecting remote IoT devices with P2P SSH download, especially on a platform like macOS, enables you to protect sensitive information from unauthorized access. This ensures that personal data, operational information, and other sensitive data remain confidential.
It's important to be aware of potential privacy concerns and to take proactive measures. A robust security approach incorporates encryption, authentication, and regular security audits to safeguard the entire ecosystem.
P2P SSH for Android
In today's interconnected world, securely connecting remote IoT devices using P2P SSH on Android has become a necessity for businesses and individuals alike. Smartphones, tablets, and other Android devices are becoming integral to the management of IoT networks. The ability to remotely control, monitor, and troubleshoot your IoT devices from your Android device provides unparalleled flexibility and agility.
The right tools are essential for securely connecting remote IoT P2P Android download solutions. These tools simplify the process and enhance the overall functionality of your IoT network, by enabling secure remote access, simplifying configuration, and optimizing network performance.
Nabto, a leading provider, offers secure P2P live streaming for smart video surveillance. They enable direct connections for P2P live streaming to your smart security camera. This eliminates the need for a central server to stream video data, which reduces latency, improves security, and increases the reliability of the live stream.
In today's digital era, securely connecting remote IoT P2P Android download has become a critical aspect of modern technology integration. Whether you're a business looking to streamline operations or an individual wanting to manage a smart home, the ability to securely connect to your devices from your Android device is essential.
Connecting remote IoT devices securely using P2P SSH on Ubuntu is a critical step in ensuring data privacy and integrity. A secure communication channel will protect sensitive data and prevent unauthorized access, and it is essential for all IoT projects.
As more devices become interconnected, the need for secure communication channels has never been more important. It is essential to secure your devices with the best tools and methods, and this will keep your system secure and efficient.
Key Advantages of Remote IoT P2P Technology: A Summary
Remote IoT P2P technology offers several advantages, which makes it ideal for a wide range of applications, from smart homes to industrial automation. Let's examine some of the most important ones:
- Enhanced Security: Direct device-to-device communication minimizes the attack surface and reduces the risk of data breaches.
- Improved Scalability: P2P networks can easily scale as more devices are added, without the need for a central server.
- Reduced Latency: Direct communication between devices eliminates the delays caused by centralized servers.
- Increased Reliability: Eliminates single points of failure, improving the system's overall robustness.
- Data Privacy: Enhanced data privacy through secure and decentralized communication.
- Cost-Effectiveness: Reduces the need for expensive central servers.
- Flexibility: Supports a wide range of devices and protocols.
By carefully considering these advantages, you can make informed decisions about implementing Remote IoT P2P technology and harnessing its potential to transform your IoT landscape.
- Lilly Gaddis Bio Age Controversies Facts Latest Updates
- Josephine Archer Cameron The Untold Story Of Linda Hamiltons Daughter
The Ultimate Guide To Remote IoT P2P Review Unlocking The Future Of

The Ultimate Guide To Remote IoT P2P Review Unlocking The Future Of

How To Securely Connect Remote IoT Devices Via P2P On Android A