SSH Key Management: Best Practices & Security Guide
Are you struggling to keep your digital infrastructure secure? Effective SSH key management is not just a technical necessity, but a cornerstone of robust cybersecurity, safeguarding your data and access to critical systems.
In the ever-evolving landscape of cybersecurity, the Secure Shell (SSH) protocol stands as a fundamental tool for secure remote access and data transmission. However, the very foundation of SSH security its keys often becomes a significant vulnerability if not properly managed. This article delves into the critical aspects of SSH key management, exploring best practices, potential risks, and strategies for maintaining a secure and efficient environment. We will navigate the complexities of SSH keys, offering insights into their creation, protection, rotation, and overall lifecycle management, equipping you with the knowledge to fortify your systems against potential threats.
SSH keys provide several benefits for protecting server access and data transmission. The public key and the private key are primary features of SSH. Properly managing these keys is crucial for maintaining secure access to your systems while avoiding common pitfalls that could compromise your security or disrupt your workflow. This guide covers essential SSH key management best practices, including key generation, protection, rotation, and backup strategies. Learning how to use these best practices is key to protecting your systems and network.
- Ava Taylor The Rise Transformation Of Rachel Bernard Now
- Tan Chuanjin His Life Career Wifes Role Insights Now
Here's a look at the importance of SSH key management and why it can be so complex. SSH key management is, essentially, the practice of managing those critical admin keys so that you know at all times:
- Who has access
- Where the keys are used
- How to revoke access when needed
Although passwordless SSH is easier to use and usually more secure than using passwords, SSH key management requires proper planning. Given the complexity, security teams often overlook SSH key management, making it one of the prime attack vectors. The complexities of SSH key management will make you exposed to errors in configuration and will make it hard to reason about security.
| Aspect | Details |
|---|---|
| Definition | SSH key management is the practice of managing Secure Shell (SSH) keys to ensure secure access and data transmission. It involves key generation, protection, rotation, and access control. |
| Importance | Crucial for maintaining secure access to systems and avoiding security compromises. Properly managed keys prevent unauthorized access, policy violations, and regulatory penalties. |
| Key Components | Includes the public and private keys. The public key is placed on the server, and the private key is kept secure by the user. |
| Benefits | Provides secure access, simplifies access compared to passwords, and is essential for various security measures. |
| Best Practices | Key generation, key protection, key rotation, access control, monitoring, and regular key audits. |
| Common Pitfalls | Unmanaged keys, lack of rotation, insecure storage, and poor access control policies. |
| Tools and Techniques | Key management tools, SSH certificates, smart cards, and hardware security modules (HSMs). |
| Regulatory Compliance | Plays a vital role in achieving and maintaining regulatory compliance in environments where SSH is used. |
| Challenges | Key proliferation, the complexity of managing numerous keys, and lack of formal key management operations. |
| Reference Website | Example.com |
An improvement over the telnet tool due to encryption, the SSH protocol enables access to remote servers and databases. Here are some of the challenges that organizations face when it comes to SSH key management:
- Marisol Yotta Bio Pics More Everything You Need To Know
- Mercedes Kilmer Life Career Val Kilmers Legacy Latest Updates
- Keys can proliferate across an organization.
- Requires proper provisioning, termination, and monitoring processes.
- Often overlooked by security teams, becoming prime attack vectors.
Unlike SSL/TLS certificates, SSH keys do not have an expiration date. That means they tend to multiply across an organization over time.
The process of properly managing SSH keys is very important to do correctly. You must ensure full coverage of your organizations keys and proper coverage of any security vulnerabilities. Following are a series of suggested best practices for proper SSH key management. Many organizations don't have a formal SSH key management ops function. SSH key management should be part of an organization's access and risk management program. That puts the onus on individual admins to do it all manually, and the experience is far from ideal.
To ensure robust protection of your infrastructure and continuous regulatory compliance, here are the best practices to follow for effective SSH key management:
- Set clear rules for SSH key use and management.
- Implement an SSH key management policy or make sure your current security policy has all the rules for proper SSH key management.
- Policies and procedures must establish consistent baseline requirements across all environments where SSH keys are used.
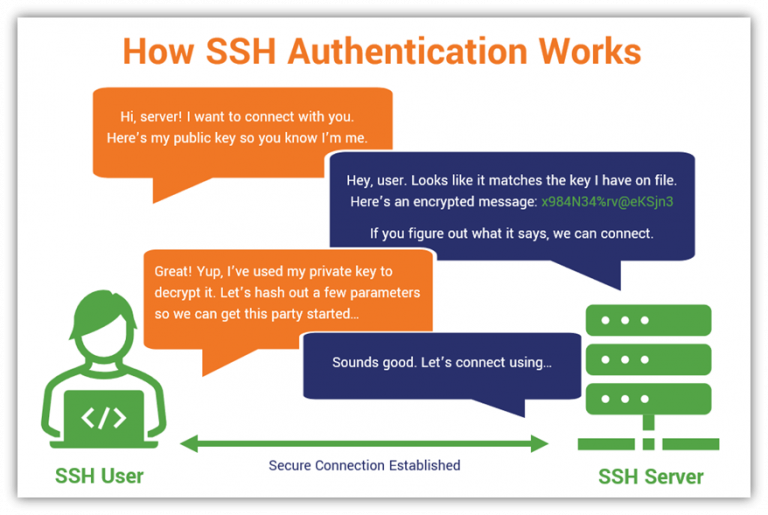
SSH keys are a way to authenticate SSH connections without using a password, either to speed up your access or as a security measure, if you turn password access off and ensure only authorized keys are permitted. To create an SSH key, run the command:
The complexities of SSH key management will make you exposed to errors in configuration and will make it hard to reason about security. Changing the keys is thus either best done using an SSH key management tool that also changes them on clients, or using certificates. Using X.509 certificates for host authentication can be an effective strategy. This way, each SSH key pair is easily identifiable.
Just like passwords, SSH keys should be changed or rotated regularly to reduce the risk of a key being used maliciously if its compromised and unnoticed. Have a clear process for revoking SSH keys when they are no longer in use or if a key might be compromised. But with the right methods, using multiple SSH keys can actually be smooth sailing instead of a pain. Whether you need keys for a personal server, work projects, client sites, or even automated scripts, understanding the fundamentals is essential.
Here are the reasons that make SSH key management challenging:
- Keys are often not tracked.
- Keys are often stored insecurely.
- It can be hard to rotate them.
- The wrong keys could be in use, and no one would know.
Recently leaked CIA hacking tools were collecting SSH keys, highlighting the importance of secure key management. Our solutions to SSH key management are focused on providing secure and easy ways to manage these critical credentials. If you're unfamiliar with SSH key management, we strongly recommend you review NIST document IR 7966, titled Security of Interactive and Automated Access Management Using Secure Shell (SSH).
One solution is to implement a central Key Management System (KMS) or a dedicated SSH key management tool. These tools often include:
- Centralized key storage
- Automated key rotation
- Key revocation capabilities
- Access control features
Often the key component of SSH key management is secure storage of keys, or implementing key rotation best practices. These things do not scale and they're too complex. Thus it is not advisable to train your users to blindly accept them.
Here are other strategies for multiple SSH keys management:
- Use descriptive filenames
- Employ a naming convention that includes the purpose of the key, the system it accesses, and the user or service it belongs to.
- Organize keys by project, environment, or user role.
- Implement key rotation policies.
- Regularly rotate keys.
- Revoke compromised or old keys immediately.
- Use automation tools.
- Use tools to automate key management tasks, such as key generation, deployment, and revocation.
- Implement access controls.
- Limit access to keys based on the principle of least privilege.
- Audit your keys and access regularly.
Aws key management service (kms) is a managed service that allows users to easily create and manage cryptographic keys used for data protection. Why I picked AWS Key Management Service:
- Centralized Key Management: AWS KMS allows you to centrally manage your cryptographic keys.
- Hardware Security Modules (HSMs): AWS KMS uses hardware security modules (HSMs) to protect your keys.
- Integration with AWS Services: AWS KMS integrates with many other AWS services.
- Audit Trails: AWS KMS provides detailed audit trails.
Best practices for SSH key management. The process of properly managing SSH keys is very important to do correctly. You must ensure full coverage of your organizations keys and proper coverage of any security vulnerabilities. Following are a series of suggested best practices for proper SSH key management:
- Key Generation: Use strong key algorithms (e.g., RSA with a minimum of 2048 bits or Ed25519). Generate keys securely and store them properly.
- Key Protection: Protect private keys using strong file permissions (e.g., 600 or stricter) and consider encrypting them with a passphrase.
- Key Rotation: Implement regular key rotation policies to minimize the impact of potential key compromises.
- Access Control: Use access controls to limit who can use which keys, and what they can access with those keys.
- Monitoring and Auditing: Implement monitoring to track key usage.
- Policy Enforcement: Establish and enforce clear policies and procedures for SSH key management.
- Regular Key Audits: Conduct regular audits to ensure that key management practices are followed and that there are no unauthorized keys.
A secure, centralized SSH key management solution can provide significant advantages, making it easier to:
- Ensure proper key rotation.
- Enforce security policies.
- Maintain an audit trail of key usage.
- Simplify access control.
- Improve overall security posture.
Something that may make you feel better, get a smartcard or something like a YubiKey. Read up on Public Key Infrastructure (PKI) and SSH. The key pair and the server's keys are just the first layer. In addition to the security risk, unmanaged SSH keys can lead to policy violations, failed audits, and massive regulatory penalties. To ensure robust protection of your infrastructure and continuous regulatory compliance, here are the best practices to follow for effective SSH key management.
Implement and consistently apply these practices to reduce vulnerabilities, maintain compliance, and enhance overall security. The key to robust SSH key management lies in a proactive approach, encompassing secure key generation, stringent access controls, regular audits, and continuous monitoring.
This publication assists organizations in understanding the basics of SSH interactive and automated access management in an enterprise, focusing on the management of SSH user keys. Best and secure SSH key management tool. Keystash solved centralized key management and user management in our Linux environment. We went with Keystash because we couldnt find another solution with the same features and the benefit has been the easiest deployment of keys to new servers which saves us time!

SSH Key Management Tools and Best Practices

Universal SSH Key Manager Zero Trust Authentication Key Management
14 SSH Key Management Best Practices You Need to Know Hashed Out by